Please Follow us on Gab, Minds, Telegram, Rumble, Truth Social, Gettr, Twitter
UPDATE: There is push back on this article. We are going to present both sides and the reader can make up his own mind...
We received this link refuting BOUNGIORNO analysis...
And we received this information supporting BOUNGIORNO:
Palm Beach Candidate for supervisor of elections Jeff Boungiorno has released information showing massive breach of the county's election systems. The data shows similar coding artifacts from Mesa County, CO of Tina Peter's fame.
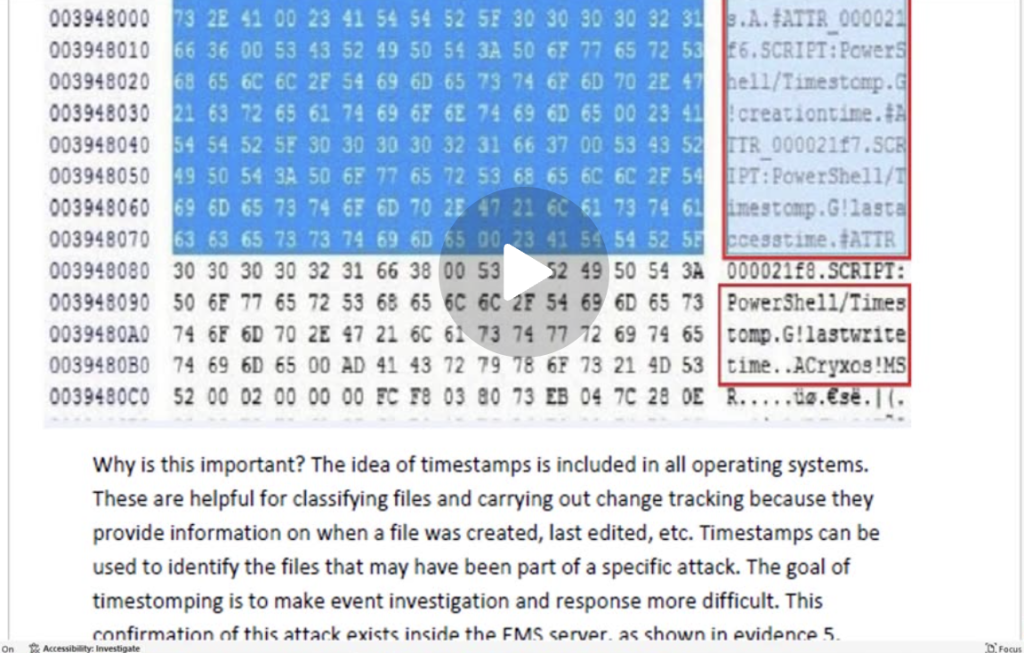
Time stomping is a technique used to alter the timestamps on files or directories in a computer system, often to cover tracks or to make it appear as if certain files were created, accessed, or modified at different times than they actually were. In the context of a Windows operating system, time stomping can be accomplished using various methods and tools.
Common Methods of Time Stomping in Windows:
- Using the
touchCommand:- The
touchcommand in Windows, when available, can be used to create or update the timestamp of a file. This is more common in Unix-like systems, but similar functionality can be replicated in Windows using PowerShell or other tools.
- The
- PowerShell Commands:
- You can use PowerShell to modify the timestamps of files. For example:powershellCopy code
(Get-Item "C:\path\to\file.txt").LastWriteTime = "01/01/2020 12:00:00"This command will change the "Last Write Time" of the specified file to the date and time provided.
- You can use PowerShell to modify the timestamps of files. For example:powershellCopy code
- Using the
SetFileTimeAPI:- Windows provides the
SetFileTimeAPI, which can be accessed through programming languages like C++ or Python to modify the creation, access, or modification times of a file.
- Windows provides the
- Third-Party Tools:
- There are various third-party tools specifically designed to perform time stomping, such as Timestomp. These tools are often used by penetration testers and sometimes by malicious actors to alter file timestamps.
- Manipulating System Time:
- Another approach is to change the system clock on the Windows machine, create or modify the files while the system time is set to the desired date, and then revert the system clock. This method is less commonly used because it may leave other traces.
- Forensic Implications:
- Time stomping can make forensic analysis more challenging, as it obscures the true timeline of file activity. However, forensic tools often look for inconsistencies in the metadata or use other artifacts to detect time stomping.
Example of Changing Timestamps Using PowerShell:
powershellCopy code$file = Get-Item "C:\path\to\file.txt"
$file.CreationTime = "01/01/2020 12:00:00"
$file.LastWriteTime = "01/01/2020 12:00:00"
$file.LastAccessTime = "01/01/2020 12:00:00"
This script will change all three timestamps (creation, last write, and last access) of the specified file to January 1, 2020, at 12:00 PM.
Mitigating Time Stomping:
To mitigate the effects of time stomping, security teams should:
- Correlate timestamps with other system logs (e.g., event logs, security logs).
- Use advanced forensic tools that can detect inconsistencies or signs of timestamp manipulation.
- Monitor for the usage of time-stomping tools or suspicious PowerShell commands.