
Please Follow us on Gab, Minds, Telegram, Rumble, Gab TV, Truth Social, Gettr, Twitter
As many people now know, many vulnerabilities have been found in the machines used to count our votes which may help types of software operations, called algorithms, affect election results. Many experts have testified to these vulnerabilities. For instance, in the video linked below, cyber threat expert & space systems operational tester, Col. Shawn Smith, provides an excellent overview of just how open to interference these systems are (watch from about 7:00 min. in to the 20 min. mark):
Return to Hand Counting, Missouri Elections, Webinar | Frank Speech the Home of Free Speech
Smith explains that the cyber threats from foreign nation states are far more serious than most people imagine, and yet there is not a single voting system used in the US that is manufactured entirely in the US. Most are entirely manufactured outside the country with non-US components, and there is neither supply chain nor manufacturing security.
Smith says any sense of security offered by the certification of voting systems by “accredited labs” is completely false and he has no doubts that our systems have never been properly tested. Talking with Clay Parikh, an Army cyber security specialist with 9 years’ experience as one of the only security testers for the Voting Systems Testing Lab, Clay told Smith he was only allowed to do basic compliance testing and was not allowed to test to the standards used by the Department of Defense. He found many vulnerabilities quickly and easily within 5-10 minutes, some in as little as 2-3 minutes. While he identified and reported hundreds of vulnerabilities, he said no corrective action was ever taken, and the voting systems were certified anyway.
It turns out that no machines are certified to standards more recent than 2005, despite the many technological advances of the last 18 years. Another significant concern is that these machines are turned over to public election officials with no cyber security background.
In Florida we have the same issues of questionable certifications using outdated, inadequate standards. According to the Division of Elections own webpage, the certifications of the machines used throughout the state were more than two years old at the time of the 2022 general election. The last certification update to the ES&S system (the most commonly used in Florida) was on May 16, 2019 and was necessitated by a modem upgrade on the DS200 machine from 3G to 4G, proving that the voting machines, which are really computers, could potentially connect to the internet. The certification memo can be seen here:
ess-evs-release-4530-version-3-memo.pdf (floridados.gov)
Florida, like many other states, receives federal funds under Section 251 of the Help America Vote Act (HAVA). These funds are administered by the Election Assistance Commission (EAC) to help states run their elections. The EAC also accredits testing laboratories and certifies voting systems. However, none of the machines used in Florida (or in California, Alabama, most of New England and several other states) are certified by the EAC.
System Certification Process | U.S. Election Assistance Commission (eac.gov)
It is not clear whether, in accepting EAC funds, Florida is bound to follow EAC certification standards, which mandate biennial recertification. The Secretary of State and at least one Supervisor of Elections (SoE) have claimed that Florida has no such obligation.
If in fact the acceptance of Federal funds does bind Florida to EAC standards, are there then grounds for eliminating the machines on the basis that, contrary to EAC rules, they all contain a device that can connect them to the internet? (We know for certain that the ES&S machines used in Miami-Dade, Palm Beach and many other counties contain a modem (and a Florida Division of Elections memo on machine certification confirms this) as tabulation results are transmitted on a private network to the SoE on Election Day. Compliance with EAC rules would result in the machines becoming unusable in any future election, or else in them all having to have their modems removed so that their data could only be collected in situ or via a thumb drive, which would open the door to a whole new set of vulnerabilities.
As they contain at least 650,000 lines of proprietary code and so not subject to independent examination, one wonders how any of these machines could ever be reliably certified. And while we would like to think elections in Florida are free and fair, we can actually look at the results themselves to prove they are not.
STATISTICALLY IMPOSSIBLE RESULTS
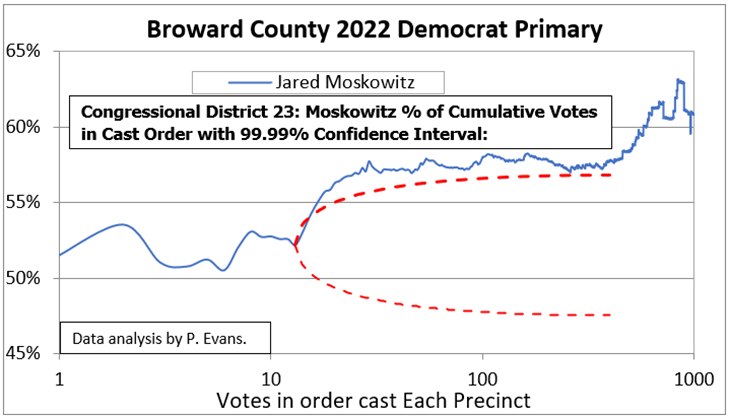
In the 2022 Primary in Palm Beach County, it is apparent that some kind of algorithm affected results. Pattern recognition expert and statistician, Phil Evans analyzed the cumulative voting pattern for various races. In his charts (see below) one can see the percentage of votes cast for a particular candidate ramping up well above the red line representing the 99.99% confidence interval (a statistical term used to predict results based on a sample). In this instance, the red curve outlines the area within which there is a 99.99% chance that the results will fall based on the first 14 votes in every precinct. For the favored candidate, however, we can see the cumulative percentage of votes (blue line) beginning to deviate from the confidence interval immediately after the 14th vote was cast in every precinct. In the District 23 Democrat primary race, Moskowitz’s percentage of the votes (the blue line) quickly climbs above the 99.99% confidence limit. The horizontal axis of the chart shows the cumulative number of votes cast, from one to 1,000, in every precinct. There is only a 0.01% (1 in 10,000) chance that the vote pattern shown here occurred naturally, without external manipulation.
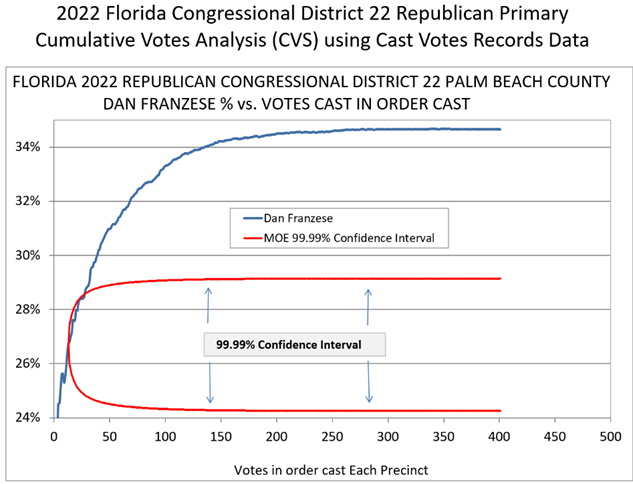
We can see this effect again in the District 22 Republican Primary chart below. Here candidate Franzese’s share of the vote climbs well above the confidence interval after the 14th vote is cast in each precinct. If his cumulative vote total was normal, we would expect, with 99.99% certainty, that it would fall between 24% and 29%, rather than the 35% he achieved.
Phil Evans has found a large number of other races similarly affected, resulting in impossible or extremely unlikely results. Given the chances of such occurrences are only one in 10,000, the fact he is finding it in many races shows something is affecting the results.
This is the kind of thing that is causing so many to question results from 2020. While Trump managed to win Florida, it was likely only made possible by the requirement for all results to be reported by midnight on election night. In this video, Florida’s results are reviewed and explained:
This longer video also explains many other anomalies seen in the election and gives background information on the results themselves:
A company called SCYTL, headquartered in Barcelona, Spain and with an R&D office in Tampa, Florida (yes, really) is responsible for election results reporting, along with another company called Clarity Elections. SCYTL’s name can be found on many official election-related webpages (see below). What has been found in a disturbingly large number of official SCYTL 2020 election results are vote batches in which Trump’s & Biden’s percentages suddenly begin to perfectly match their total vote percentages.
Let us say that at some point, the total votes were split 48.5% for Trump and 51.5% for Biden. The next reported batch would come in at that same 48.5% for Trump and 51.5% for Biden. It would be strange enough for this to happen once, but for it to happen repeatedly is a statistical impossibility. Also, to have many consecutive batches come in at exactly the same percentages for each candidate is just as improbable, even impossible, and results in the curious phenomenon of fractional votes: if an algorithm is designed to produce a particular percentage of votes for a candidate, it will have to do so by dividing the number of actual votes to reflect that percentage. Since in most cases the number of votes does not evenly multiply by the required percentage to a whole number, this results in nearly every batch having fractional votes which are clearly algorithmic fictions: there can only be whole numbers of real votes. SCYTL surely has some serious explaining to do to account for these phenomena.
Clint Curtis, a registered Democrat & former computer programmer for multiple federal agencies, testified to Congress in 2004 that he was contracted to write a prototype program for Florida Rep. Tom Feeney that would “flip the vote 51-49 to whoever you wanted it to go to and whichever race you wanted to win”. Asked if such a program was detectable by election officials, Curtis said they would “never see it”. He also testified before the Arizona Elections Committee just recently that any computer-based voting machine is vulnerable to tampering. Fixing election results using a program, he said, is “very easy to do” but “hard to stop”.
MACHINE VULNERABLILITIES
We could speak endlessly about the vulnerabilities in the election systems used in this country. Everything from almost nonexistent SQL database security to wireless connections, to USB drives. We know the tabulators have wireless modems and connect to an intranet. What is to stop them from being remotely accessed through that same modem? We know the voter check-in system is constantly checking the voter database to confirm voters are eligible, have not yet voted and record when they have. Vote tabulators are programmed to receive input from removable media, namely USB drives. These USB drives are proprietary to the machine manufacturer. We have no way of knowing what is on them. At some point a USB drive is programmed and needs to be on a network, open or closed. Even on a closed network, a USB drive is extremely vulnerable during programming. The military does not allow use of USB ports, for good reason. Per elections systems technical expert Bennie Smith, USB ports and their devices are the most threatening equipment for a computer.
Jake Stauffer, a former cyber analyst for the U.S. Air Force, looked inside the ES&S DS200 tabulator:
“What we found…it was staggering. There were multiple vulnerabilities that could allow an attacker to get the highest level of access to the system. We found multiple operating system patches missing – what that means is that an attacker can inject code into that system, execute that with the possibility of receiving some sort of control. When ES&S discovered that we were not using their testing plans, they were appalled when we used our own testing plan and found these vulnerabilities, they pretty much told us that they had their own team, that they were not interested. How can a vendor sell a voting system with this many vulnerabilities? I can’t find the answer.”
Very recently, in the Dominion Voting Systems v Fox News legal case, there was a “Bombshell Legal Filing” which exposed that Dominion executives knew their system was riddled with issues. Just weeks before the 2020 presidential election, Dominion’s Director of Product Strategy and Security, Eric Coomer, acknowledged in private that “our shit is just riddled with bugs.”
Indeed, Coomer had been castigating Dominion’s failures for years. In 2019, Coomer noted that “our products suck.” He lamented that “most all (sic)” of Dominion’s technological failings were “due to our complete f— up in installation.” In another instance, he identified a “*critical* bug leading to INCORRECT results.” He went on to note: “It does not get much worse than that.” And while many companies might have resolved their errors, Coomer lamented that “we don’t address our weaknesses effectively!”
Employees of the companies were not the only ones aware of the issues: an older 2009 study out of the University of Pennsylvania noted extreme deficiencies. From the report, Security Evaluation of ES&S Voting Machines and Election Management System, Department of Computer and Information Science University of Pennsylvania (https://www.cs.swarthmore.edu/~aviv/papers/ess-evt08.pdf):
This paper summarizes a security analysis of the DRE and optical scan voting systems manufactured by Election Systems and Software (ES&S), as used in Ohio (and many other jurisdictions inside and outside the US).
We found numerous exploitable vulnerabilities in nearly every component of the ES&S system. These vulnerabilities enable attacks that could alter or forge precinct results, install corrupt firmware, and erase audit records. Our analysis focused on architectural issues in which the interactions between various software and hardware modules leads to systemic vulnerabilities that do not appear to be easily countered with election procedures or software updates. (Emphasis added.)
And in Section 4 - “Systemic and Architectural Issues” of the same paper:
There are fundamental security deficiencies throughout the ES&S Unity EMS, iVotronic DRE and M100 optical scanner software and hardware. Virtually every mechanism for assuring the integrity of precinct results and for protecting the back-end tallying system can be circumvented. Election results can be tampered within the ES&S system by exploiting any of a number of different vulnerabilities that were discovered. The normal access provided to individual precinct poll workers (and in some cases to voters themselves) is sufficient to conduct attacks that alter county-wide election results and that, in some cases, cannot be detected or recovered from through audits or recounts. Perhaps more importantly, we show how the interaction of the various software and hardware modules leads to systemic vulnerabilities that can spread throughout the system. There is a strong potential for practical attacks that propagate “virally” from the field back to the county election management system. That is, a single circumvented piece of precinct hardware (such as a memory card returned from a precinct for vote tallying) can effectively “take over” the county-wide back-end tally system, alter county-wide results reported in the current election, and then corrupt the installed firmware of additional precinct hardware in subsequent elections. The broad scope of such attacks provides great leverage to the adversary and can be extraordinarily difficult to detect, trace, or recover from. (Emphasis added.)
By knowing about, but not disclosing these issues, Dominion likely violated Florida Statute 101.56065 - “Voting system defects; disclosure; investigations; penalties”:
(2)(a) On January 1 of every odd-numbered year, each vendor shall file a written disclosure with the department identifying any known defect in the voting system or the fact that there is no known defect, the effect of any defect on the operation and use of the approved voting system, and any known corrective measures to cure a defect, including, but not limited to, advisories and bulletins issued to system users. (Emphasis added.)
This statute also states:
“If a vendor fails to file a required disclosure for a voting system previously approved by the department, that system may not be sold, leased, or used for elections in the state until it has been submitted for examination and approval and adopted for use pursuant to s. 101.5605. The department shall provide written notice to all supervisors of elections that the system is no longer approved.” (Emphasis added.)
‘NO AD’ subscription for CDM! Sign up here and support real investigative journalism and help save the republic!‘
I believe that, by their Director of Product Strategy & Security’s admissions, unless Dominion filed a report on January 1st of 2019, 2021 or 2023 disclosing such defects, our Department of State needs to immediately suspend use of their system in the State of Florida. Likewise, if issues exist within the ES&S system and they have not filed a similar disclosure report, their system should likewise be suspended from use by the Department of State. If these issues have in fact been disclosed, what has been done to ensure they have been satisfactorily addressed, and why was the use of machines never suspended?
Finally, I will quote Florida Statute 101.015:
The division (of Elections) shall also develop methods to determine the will of the public with respect to voting systems.
Numerous counties around the country have voted to remove election machines and return to manual hand counting. How many Floridians have lost faith in computerized election systems? A CNN poll from last year showed that only 16% of those surveyed were “very confident” that our elections reflected the will of the people.
The state needs to wake up to the fact that the electronic vote tabulating systems are too easily compromised; our election results prove it and voters know it.



















The data presented proves to any reasonable minded person that our computer voting systems in ALL of America is simply compromised and corrupt. Florida has the golden opportunity to correct this issue...a simple one...use only paper votes/ballots. If not, a ham sandwich or a Fetterman type will be guaranteed the next President...no campaigning or debating...just stay home and be elected by the totally broken/corrupt system in place now. I truly believe if this issue isn't resolved before 2024 our country is lost as a constitutional republic. Just my two cents.